How the Eaton Gigabit Network Card protects against supply chain cyber attacks
2:22
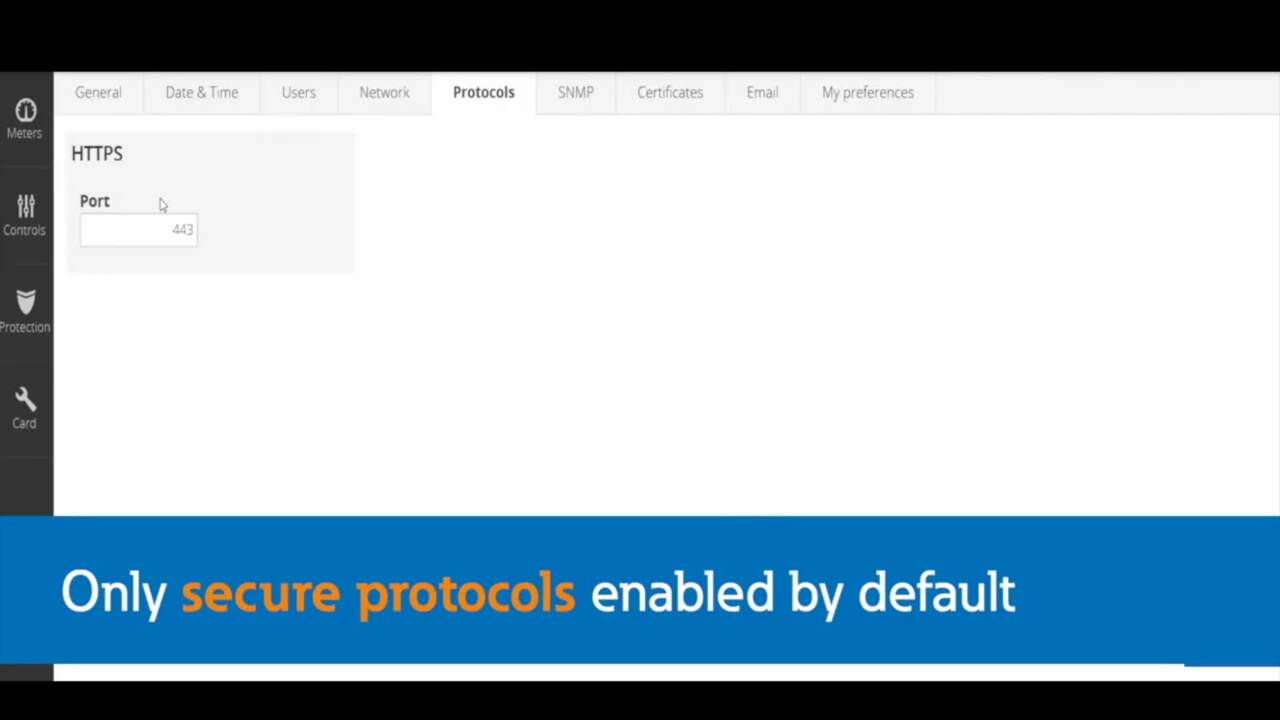
Eaton’s Network-M2 card for power quality connectivity provides protection from a supply chain attack. In addition to enterprise standard information security mitigations, feature branches undergo an independent code review process before being merged. M2 firmware is digitally signed, preventing the installation of unauthorized or corrupted firmware. M2 firmware is encrypted, preventing analysis for vulnerabilities. The M2 file system is digitally signed, preventing unauthorized changes to your data. Eaton’s Nework-M2 card transforms a UPS or Uninterruptable Power Supply into an enterprise level IoT device. Learn more at https://www.eaton.com/cybersecurity
Eaton’s Network-M2 card for power quality connectivity provides protection from a supply chain attack. In addition to enterprise standard information security mitigations, feature branches undergo an independent code review process before being merged. M2 firmware is digitally signed, preventing the installation of unauthorized or corrupted firmware. M2 firmware is encrypted, preventing analysis for vulnerabilities. The M2 file system is digitally signed, preventing unauthorized changes to your data. Eaton’s Nework-M2 card transforms a UPS or Uninterruptable Power Supply into an enterprise level IoT device. Learn more at https://www.eaton.com/cybersecurity
Related videos for "eaton gigabit network"
-
The Eaton Gigabit Network Card for cybersecurity
1:19
As a leader in UPSs (uninterruptible power supplies), Eaton launched the Gigabit Network Card for additional cybersecurity and also faster speeds.
-
Eaton Gigabit Network-M3 card – Enhanced capabilities, unmatched security
0:15
Eaton Gigabit Network-M3 card – Enhanced capabilities, unmatched security
-
Eaton Gigabit Network Card (Network-M3): Overview
8:21
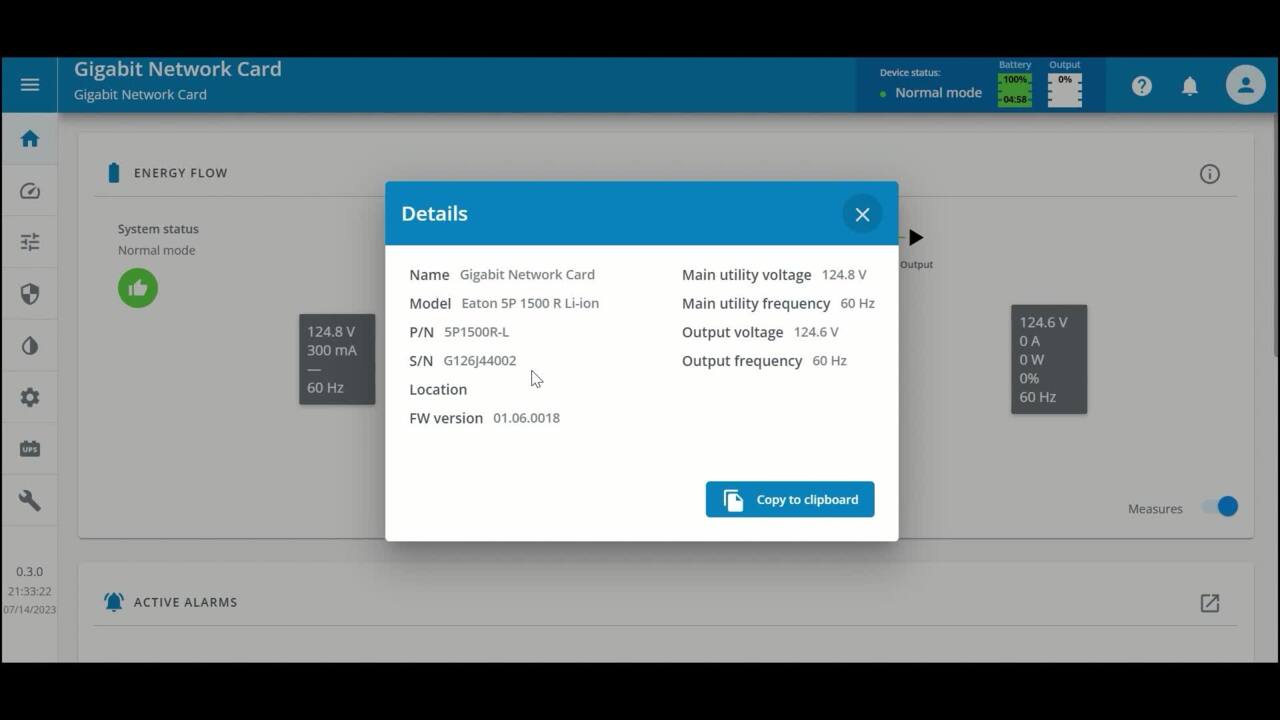
Eaton's latest network management card improves business continuity by providing warnings of pending issues to administrators and helping to perform orderly shutdown of servers and storage.