Eaton DS-VFI transformer
3:06
Eaton’s Cooper Power series Dual Source VFI (DS-VFI) transformer provides automatic source recovery, built-in overcurrent protection and grid automation schemes for the modern electrical distribution system. Designed for both main-main applications and loop-feed applications, the DS-VFI transformer combines state-of-the-art switchgear controls and automation with proven high-efficiency liquid-filled transformer technology into a single assembly. The solution enables complete medium-to low-voltage distribution protection and automatic outage restoration in a compact, cost-effective package.
Eaton’s Cooper Power series Dual Source VFI (DS-VFI) transformer provides automatic source recovery, built-in overcurrent protection and grid automation schemes for the modern electrical distribution system. Designed for both main-main applications and loop-feed applications, the DS-VFI transformer combines state-of-the-art switchgear controls and automation with proven high-efficiency liquid-filled transformer technology into a single assembly. The solution enables complete medium-to low-voltage distribution protection and automatic outage restoration in a compact, cost-effective package.
Cooper Power series Similar Videos
-
Medium-voltage switchgear fundamentals | Eaton PSEC
15:50
Explore medium-voltage switchgear types including metal-clad, metal-enclosed, and compact switchgear. Learn key standards, design features, and advancements that enhance reliability, reduce downtime, and improve protection in power systems.
-
Utility overvoltage protection with surge arresters | Eaton PSEC
9:06
Learn how surge arresters protect utility distribution equipment from overvoltage’s, caused primarily by lightning. Also, discover how arresters work, sizing considerations, and their role in maintaining the reliability of utility infrastructure.
-
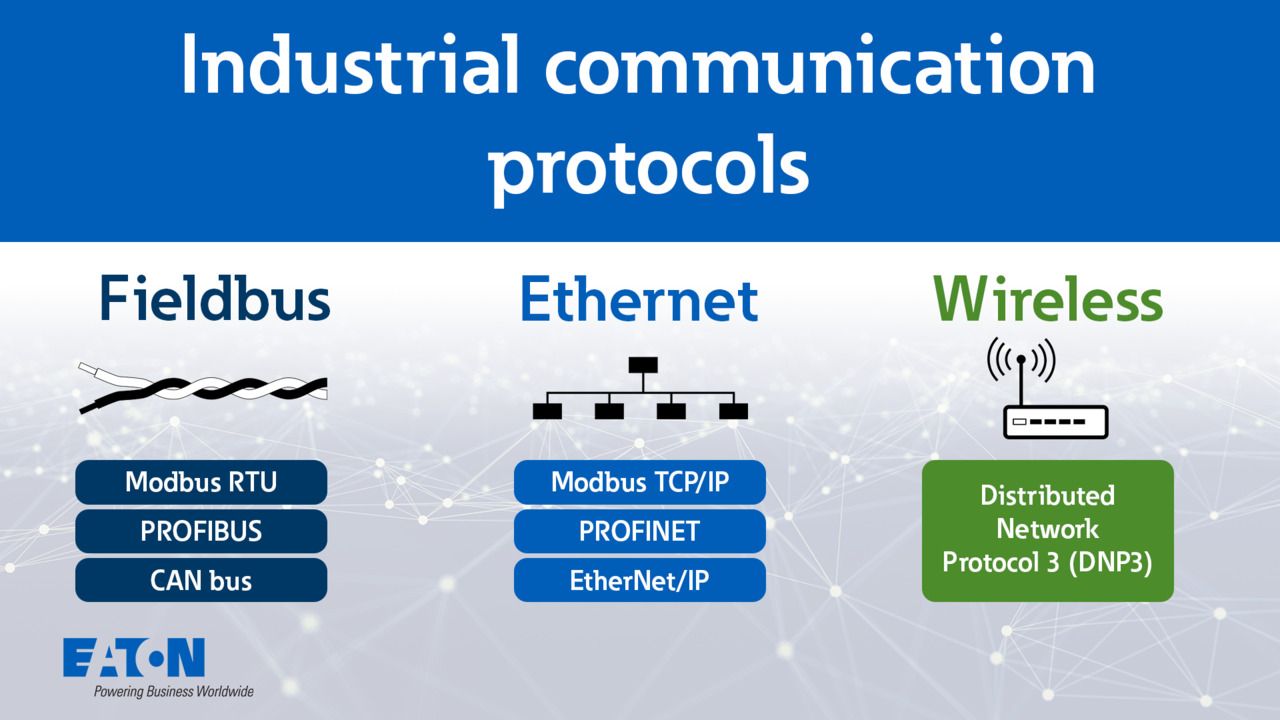
Industrial communication protocols explained | Eaton PSEC
12:23
Learn about industrial communication protocols such as Fieldbus, Ethernet, and wireless communications. Understand how they operate, their features, limitations, and cybersecurity standards.