06-Pow-R-Way III busway wall penetration installation
1:05
With a customizable and flexible design, Pow-R-Way III busway is the preferred means of connecting electrical equipment to maximize power distribution system performance. Its ease of use and speed of installation provides an efficient solution for even the most challenging layout requirements compared to traditional cabling conduit solutions. This wall penetration installation video is part of the Pow-R-Way III instructional series to walk you through the busway’s set-up and deployment. Learn more at https://www.eaton.com/us/en-us/catalog/low-voltage-power-distribution-controls-systems/pow-r-way-III-busway.html
With a customizable and flexible design, Pow-R-Way III busway is the preferred means of connecting electrical equipment to maximize power distribution system performance. Its ease of use and speed of installation provides an efficient solution for even the most challenging layout requirements compared to traditional cabling conduit solutions. This wall penetration installation video is part of the Pow-R-Way III instructional series to walk you through the busway’s set-up and deployment. Learn more at https://www.eaton.com/us/en-us/catalog/low-voltage-power-distribution-controls-systems/pow-r-way-III-busway.html
Electrical - 100 latest videos Similar Videos
-
Get it Done Today with Eaton
1:13
With a commitment to stocking popular light commercial solutions, distributors who participate in Eaton’s Pow-R-Xpress program are helping contractors get it done today.
-
Electrical faults explained: types, causes, calculations, and protection | Eaton PSEC
10:02
Learn about electrical faults, including short circuits, ground faults, and arcing faults and how to protect against them with circuit protection devices. Understand the importance of time current curves for safety and troubleshooting.
-
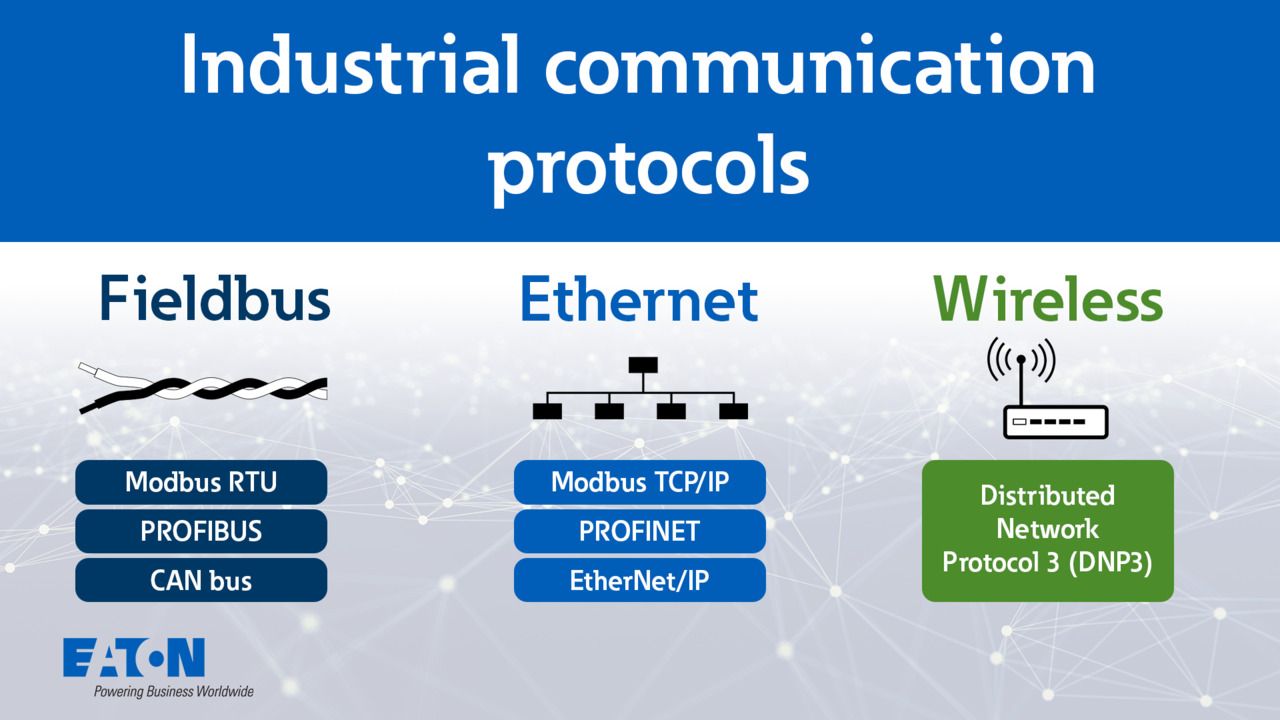
Industrial communication protocols explained | Eaton PSEC
12:23
Learn about industrial communication protocols such as Fieldbus, Ethernet, and wireless communications. Understand how they operate, their features, limitations, and cybersecurity standards.